ᱨᱩᱠᱷᱤᱭᱟᱹ ᱚᱰᱤᱴ
ᱢᱤᱫ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱚᱰᱤᱴ ᱯᱞᱟᱜᱤᱱ
ᱨᱩᱠᱷᱤᱭᱟᱹ ᱚᱰᱤᱴ ᱞᱟᱹᱜᱤᱫ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱯᱞᱟᱜᱤᱱ
ᱟᱢᱟᱜ ᱥᱮᱨᱵᱷᱟᱨ ᱟᱨ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱮ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱚᱰᱤᱴ ᱪᱟᱹᱞᱩ ᱞᱟᱹᱜᱤᱫ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱯᱞᱟᱜᱤᱱ ᱾
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱟᱞᱜᱟ ᱢᱮ
ᱟᱢᱟᱜ ᱣᱮᱵᱽ ᱩᱛᱱᱟᱹᱣ ᱠᱟᱹᱢᱤ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱞᱟᱹᱜᱤᱫ ᱟᱞᱮᱭᱟᱜ ᱠᱞᱟᱣᱰ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱟᱲᱮ ᱨᱮᱭᱟᱜ ᱞᱟᱵᱷ ᱞᱟᱹᱜᱤᱫ ᱰᱤᱡᱟᱭᱤᱱ ᱟᱠᱟᱱᱟ
ᱟᱞᱜᱟ ᱪᱟᱹᱞᱩ ᱟᱨ ᱵᱚᱱᱫᱚ ᱵᱩᱛᱟᱢ
Quickly control your site's security features
ᱟᱢᱟᱜ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱧᱮᱞ ᱢᱮ
ᱨᱩᱠᱷᱤᱭᱟᱹ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱞᱟᱹᱜᱤᱫ ᱡᱟᱦᱟᱸ ᱚᱠᱛᱚ ᱨᱮᱜᱮ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱠᱮᱱ ᱮᱦᱚᱵ ᱢᱮ᱾
ᱨᱩᱠᱷᱤᱭᱟᱹ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ
ᱟᱹᱱᱟᱹᱭᱠᱟᱹᱣ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱜᱟᱹᱠᱷᱩᱲᱤᱭᱟᱹ ᱦᱚᱛᱮᱛᱮ ᱵᱮᱱᱟᱣ ᱟᱠᱟᱱ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱟᱯᱟᱵ ᱵᱮᱵᱷᱟᱨ ᱢᱮ
ᱟᱞᱜᱟ ᱟᱨ ᱞᱮᱵᱽᱲᱮᱡ ᱜᱚᱱᱚᱝ
᱑᱔ ᱢᱟᱦᱟᱸ ᱴᱟᱠᱟ ᱨᱩᱣᱟᱹᱲ ᱜᱮᱨᱮᱱᱴᱤ ᱾ ᱥᱮᱨᱢᱟᱠᱤᱭᱟᱹ ᱟᱨ ᱪᱟᱸᱫᱚ ᱯᱚᱱᱛᱷᱟ ᱢᱮᱱᱟᱜᱼᱟ ᱾
ᱥᱴᱟᱨᱴᱟᱨ
᱒᱐% ᱵᱟᱧᱪᱟᱣ ᱢᱮ
ᱞᱮᱠᱟᱛᱮ ᱵᱤᱞ ᱟᱠᱟᱱᱟ $499.99 ᱥᱮᱨᱢᱟ ᱯᱤᱪᱷᱤ ᱰᱚᱞᱟᱨ
ᱥᱟᱶᱛᱮ ᱥᱮᱨᱢᱟᱠᱤᱭᱟᱹ ᱵᱟᱧᱪᱟᱣ $99.89 ᱭᱩᱮᱥ ᱰᱚᱞᱟᱨ
ᱩᱥᱟᱹᱨᱟ ᱟᱯᱰᱮᱴ ᱵᱩᱛᱟᱢ
ᱯᱟᱹᱨᱥᱤ ᱨᱮ ᱤᱱᱥᱴᱚᱞ ᱫᱤᱥᱦᱩᱫᱤᱥ
ᱯᱚᱨᱢᱟᱱ ᱟᱠᱟᱱ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱤᱧᱡᱤᱱᱤᱭᱟᱨ ᱠᱚ
᱑ ᱦᱟᱯᱛᱟᱠᱤᱭᱟᱹ ᱥᱮᱰᱭᱩᱞᱰ ᱥᱠᱮᱱ
ᱞᱟᱦᱟᱱᱛᱤ
ᱠᱩᱥᱤᱭᱟᱜ ᱒᱕% ᱵᱟᱧᱪᱟᱣ ᱢᱮ
ᱞᱮᱠᱟᱛᱮ ᱵᱤᱞ ᱟᱠᱟᱱᱟ $999.99 ᱥᱮᱨᱢᱟ ᱯᱤᱪᱷᱤ ᱰᱚᱞᱟᱨ
ᱥᱟᱶᱛᱮ ᱥᱮᱨᱢᱟᱠᱤᱭᱟᱹ ᱵᱟᱧᱪᱟᱣ $199.89 ᱭᱩᱮᱥ ᱰᱚᱞᱟᱨ
ᱩᱥᱟᱹᱨᱟ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱵᱚᱫᱚᱞ ᱵᱩᱛᱟᱢ
ᱯᱞᱟᱜᱤᱱ ᱤᱱᱥᱴᱚᱞ ᱥᱟᱯᱚᱨᱴ
᱑ ᱫᱤᱱᱟᱹᱢ ᱥᱮᱰᱭᱩᱞᱰ ᱥᱠᱮᱱ
ᱮᱱᱴᱚᱨᱯᱨᱟᱭᱤᱡᱽ
᱓᱐% ᱵᱟᱧᱪᱟᱣ ᱢᱮ
ᱞᱮᱠᱟᱛᱮ ᱵᱤᱞ ᱟᱠᱟᱱᱟ $1,999.99 ᱥᱮᱨᱢᱟ ᱯᱤᱪᱷᱤ ᱰᱚᱞᱟᱨ
ᱥᱟᱶᱛᱮ ᱥᱮᱨᱢᱟᱠᱤᱭᱟᱹ ᱵᱟᱧᱪᱟᱣ $399.89 ᱭᱩᱮᱥ ᱰᱚᱞᱟᱨ
ᱯᱟᱥᱣᱟᱨᱰ ᱚᱰᱤᱴ ᱪᱮᱠ
ᱟᱵᱚ ᱯᱞᱟᱜᱤᱱ ᱤᱱᱥᱴᱚᱞ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ ᱵᱚᱱ
ᱵᱤᱱ ᱥᱤᱢᱟᱹ ᱥᱮᱰᱭᱩᱞᱰ ᱥᱠᱮᱱ
ᱜᱚᱱᱚᱝ ᱯᱮᱠᱮᱡᱽ ᱛᱩᱞᱟᱹ ᱡᱚᱠᱷᱟᱭ ᱢᱮ
| ᱥᱴᱟᱨᱴᱟᱨ | ᱞᱟᱦᱟᱱᱛᱤ ᱱᱚᱶᱟ ᱠᱚ | ᱮᱱᱴᱚᱨᱯᱨᱟᱭᱤᱡᱽ | |
|---|---|---|---|
| ᱵᱤᱜᱽᱭᱟᱯ ᱯᱷᱨᱤ | |||
| ᱵᱽᱨᱟᱱᱰᱤᱝ ᱯᱷᱨᱤ | |||
| ᱒ᱮᱯᱷ ᱮ ᱪᱮᱠ | |||
| ᱒᱔/᱗ ᱴᱤᱠᱤᱴ ᱜᱚᱲᱚ | |||
| ᱯᱨᱤᱢᱤᱭᱟᱢ ᱜᱨᱟᱦᱟᱠ ᱜᱚᱲᱚ | |||
| ᱯᱞᱟᱜᱤᱱ ᱟᱨ ᱛᱷᱤᱢ ᱵᱷᱟᱞᱱᱟᱨᱮᱵᱤᱞᱤᱴᱤ ᱢᱚᱱᱤᱴᱚᱨᱤᱝ | |||
| ᱢᱟᱭᱮᱥᱠᱩᱭᱮᱞ ᱵᱟᱝᱠᱷᱟᱱ ᱢᱟᱨᱤᱭᱟᱰᱤᱵᱤ ᱵᱷᱟᱨᱥᱚᱱ ᱧᱮᱞ ᱢᱮ | |||
| HTTP ᱠᱷᱚᱱ HTTPS ᱨᱤᱰᱟᱭᱨᱮᱠᱴ ᱧᱮᱞ ᱢᱮ | |||
| ᱓᱗ ᱢᱩᱴ ᱪᱮᱠ | |||
| ᱑᱐᱐ ᱠᱷᱚᱱ ᱦᱚᱸ ᱵᱟᱹᱲᱛᱤ ᱯᱟᱹᱨᱥᱤ ᱥᱟᱯᱚᱨᱴ ᱟᱠᱟᱱᱟ | |||
| ᱩᱥᱟᱹᱨᱟ ᱟᱯᱰᱮᱴ ᱵᱩᱛᱟᱢ | |||
| ᱩᱥᱟᱹᱨᱟ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱵᱚᱫᱚᱞ ᱵᱩᱛᱟᱢ | |||
| ᱯᱟᱥᱣᱟᱨᱰ ᱚᱰᱤᱴ ᱪᱮᱠ | |||
| ᱯᱟᱹᱨᱥᱤ ᱨᱮ ᱤᱱᱥᱴᱚᱞ ᱫᱤᱥᱦᱩᱫᱤᱥ | |||
| ᱯᱞᱟᱜᱤᱱ ᱤᱱᱥᱴᱚᱞ ᱥᱟᱯᱚᱨᱴ | |||
| ᱟᱵᱚ ᱯᱞᱟᱜᱤᱱ ᱤᱱᱥᱴᱚᱞ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ ᱵᱚᱱ | |||
| ᱯᱚᱨᱢᱟᱱ ᱟᱠᱟᱱ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱤᱧᱡᱤᱱᱤᱭᱟᱨ ᱠᱚ | |||
| ᱑ ᱦᱟᱯᱛᱟᱠᱤᱭᱟᱹ ᱥᱮᱰᱭᱩᱞᱰ ᱥᱠᱮᱱ | |||
| ᱑ ᱫᱤᱱᱟᱹᱢ ᱥᱮᱰᱭᱩᱞᱰ ᱥᱠᱮᱱ | |||
| ᱵᱤᱱ ᱥᱤᱢᱟᱹ ᱥᱮᱰᱭᱩᱞᱰ ᱥᱠᱮᱱ | |||
| ᱟᱨᱦᱚᱸ ᱯᱷᱤᱪᱟᱨ ᱠᱚ - ᱞᱚᱜᱚᱱ ᱜᱮ ᱦᱤᱡᱩᱜ ᱠᱟᱱᱟ |
|
ᱥᱴᱟᱨᱴᱟᱨ
|
ᱞᱟᱦᱟᱱᱛᱤ
ᱱᱚᱶᱟ ᱠᱚ
|
ᱮᱱᱴᱚᱨᱯᱨᱟᱭᱤᱡᱽ
|
|
|---|---|---|---|
| ᱵᱤᱜᱽᱭᱟᱯ ᱯᱷᱨᱤ | |||
| ᱵᱽᱨᱟᱱᱰᱤᱝ ᱯᱷᱨᱤ | |||
| ᱒ᱮᱯᱷ ᱮ ᱪᱮᱠ | |||
| ᱒᱔/᱗ ᱴᱤᱠᱤᱴ ᱜᱚᱲᱚ | |||
| ᱯᱨᱤᱢᱤᱭᱟᱢ ᱜᱨᱟᱦᱟᱠ ᱜᱚᱲᱚ | |||
| ᱯᱞᱟᱜᱤᱱ ᱟᱨ ᱛᱷᱤᱢ ᱵᱷᱟᱞᱱᱟᱨᱮᱵᱤᱞᱤᱴᱤ ᱢᱚᱱᱤᱴᱚᱨᱤᱝ | |||
| ᱢᱟᱭᱮᱥᱠᱩᱭᱮᱞ ᱵᱟᱝᱠᱷᱟᱱ ᱢᱟᱨᱤᱭᱟᱰᱤᱵᱤ ᱵᱷᱟᱨᱥᱚᱱ ᱧᱮᱞ ᱢᱮ | |||
| HTTP ᱠᱷᱚᱱ HTTPS ᱨᱤᱰᱟᱭᱨᱮᱠᱴ ᱧᱮᱞ ᱢᱮ | |||
| ᱓᱗ ᱢᱩᱴ ᱪᱮᱠ | |||
| ᱑᱐᱐ ᱠᱷᱚᱱ ᱦᱚᱸ ᱵᱟᱹᱲᱛᱤ ᱯᱟᱹᱨᱥᱤ ᱥᱟᱯᱚᱨᱴ ᱟᱠᱟᱱᱟ | |||
| ᱩᱥᱟᱹᱨᱟ ᱟᱯᱰᱮᱴ ᱵᱩᱛᱟᱢ | |||
| ᱩᱥᱟᱹᱨᱟ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱵᱚᱫᱚᱞ ᱵᱩᱛᱟᱢ | |||
| ᱯᱟᱥᱣᱟᱨᱰ ᱚᱰᱤᱴ ᱪᱮᱠ | |||
| ᱯᱟᱹᱨᱥᱤ ᱨᱮ ᱤᱱᱥᱴᱚᱞ ᱫᱤᱥᱦᱩᱫᱤᱥ | |||
| ᱯᱞᱟᱜᱤᱱ ᱤᱱᱥᱴᱚᱞ ᱥᱟᱯᱚᱨᱴ | |||
| ᱟᱵᱚ ᱯᱞᱟᱜᱤᱱ ᱤᱱᱥᱴᱚᱞ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ ᱵᱚᱱ | |||
| ᱯᱚᱨᱢᱟᱱ ᱟᱠᱟᱱ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱤᱧᱡᱤᱱᱤᱭᱟᱨ ᱠᱚ | |||
| ᱑ ᱦᱟᱯᱛᱟᱠᱤᱭᱟᱹ ᱥᱮᱰᱭᱩᱞᱰ ᱥᱠᱮᱱ | |||
| ᱑ ᱫᱤᱱᱟᱹᱢ ᱥᱮᱰᱭᱩᱞᱰ ᱥᱠᱮᱱ | |||
| ᱵᱤᱱ ᱥᱤᱢᱟᱹ ᱥᱮᱰᱭᱩᱞᱰ ᱥᱠᱮᱱ | |||
| ᱟᱨᱦᱚᱸ ᱯᱷᱤᱪᱟᱨ ᱠᱚ - ᱞᱚᱜᱚᱱ ᱜᱮ ᱦᱤᱡᱩᱜ ᱠᱟᱱᱟ |
ᱪᱮᱛᱟᱱ ᱫᱟᱢ ᱨᱮ ᱟᱢᱟᱜ ᱵᱤᱞᱤᱝ ᱴᱷᱤᱠᱟᱹᱱᱟ ᱞᱮᱠᱟᱛᱮ ᱞᱟᱹᱜᱩᱜ ᱴᱮᱠᱥ ᱵᱟᱝ ᱥᱮᱞᱮᱫ ᱢᱮᱱᱟᱜᱼᱟ ᱾ ᱯᱮᱢᱮᱱᱴ ᱢᱩᱪᱟᱹᱫᱚᱜ ᱞᱟᱦᱟᱨᱮ, ᱢᱩᱪᱟᱹᱫ ᱜᱚᱱᱚᱝ ᱫᱚ ᱪᱮᱠᱟᱣᱩᱴ ᱥᱟᱦᱴᱟ ᱨᱮ ᱩᱫᱩᱜᱚᱜᱼᱟ
ᱯᱮᱢᱮᱱᱴ ᱦᱚᱨᱟ ᱠᱚ ᱥᱤᱠᱟᱨ ᱟᱠᱟᱱᱟ
ᱴᱟᱠᱟ ᱨᱩᱣᱟᱹᱲ ᱜᱮᱨᱮᱱᱴᱤ
ᱪᱮᱥᱴᱟᱭ ᱢᱮ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱚᱰᱤᱴ ᱑᱔ ᱢᱟᱦᱟᱸ ᱞᱟᱹᱜᱤᱫ ᱟᱞᱮᱭᱟᱜ ᱴᱟᱠᱟ ᱨᱩᱣᱟᱹᱲ ᱜᱮᱨᱮᱱᱴᱤ ᱥᱟᱶᱛᱮ ᱾
ᱮᱥ ᱮᱥ ᱮᱞ ᱮᱱᱠᱨᱤᱯᱴᱮᱰ ᱯᱮᱢᱮᱱᱴ
ᱟᱢᱟᱜ ᱵᱟᱰᱟᱭ ᱒᱕᱖-ᱵᱤᱴ ᱮᱥᱮᱥᱮᱞ ᱮᱱᱠᱨᱤᱯᱥᱚᱱ ᱦᱚᱛᱮᱛᱮ ᱨᱟᱠᱷᱟ ᱢᱮᱱᱟᱜᱼᱟ ᱾
ᱪᱮᱥᱴᱟᱭ ᱢᱮ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱚᱰᱤᱴ ᱑᱔ ᱢᱟᱦᱟᱸ ᱞᱟᱹᱜᱤᱫ ᱟᱞᱮᱭᱟᱜ ᱴᱟᱠᱟ ᱨᱩᱣᱟᱹᱲ ᱜᱮᱨᱮᱱᱴᱤ ᱥᱟᱶᱛᱮ ᱾
ᱨᱩᱠᱷᱤᱭᱟᱹ ᱚᱰᱤᱴ ᱟᱭᱢᱟ ᱞᱮᱠᱟ ᱛᱮ ᱵᱮᱵᱷᱟᱨᱚᱜ ᱠᱟᱱᱟ
ᱟᱢ ᱵᱮᱵᱷᱟᱨ ᱫᱟᱲᱮᱭᱟᱜᱼᱟᱢ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱚᱰᱤᱴᱮᱴᱟᱜ ᱮᱴᱟᱜ ᱩᱫᱳᱜᱽ, ᱯᱷᱮᱥᱚᱱ ᱟᱨ ᱜᱟᱶᱛᱟ ᱠᱚ ᱨᱮ ᱾ ᱟᱢᱟᱜ ᱡᱚᱥ ᱯᱩᱨᱟᱹᱣ ᱞᱟᱹᱜᱤᱫ ᱱᱚᱣᱟ ᱫᱚ ᱞᱟᱹᱠᱛᱤᱭᱟᱱ ᱡᱤᱱᱤᱥ ᱠᱟᱱᱟ ᱾
As an entrepreneur, you're always on the go and don't have much time to spare. However, you still care about your customers and your reputation. Keep your website secure with ease by auditing the security settings.
ᱟᱢᱟᱜ ᱚᱱᱞᱟᱭᱤᱱ ᱢᱟᱹᱱ ᱫᱚ ᱟᱢᱟᱜ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱦᱚᱛᱮᱛᱮ ᱮᱥᱮᱨ ᱟᱠᱟᱱᱟ ᱾ ᱟᱢᱟᱜ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱟᱫᱷᱟᱨᱚᱱ ᱥᱮᱴᱤᱝ ᱥᱟᱶᱛᱮ ᱨᱟᱠᱷᱟ ᱫᱚᱦᱚᱭ ᱢᱮ ᱟᱨ ᱱᱚᱣᱟ ᱟᱯᱰᱮᱴ ᱫᱚᱦᱚᱭ ᱢᱮ ᱾
ᱟᱢ ᱯᱨᱚᱯᱷᱮᱥᱚᱱᱟᱞᱤᱡᱽ ᱞᱟᱹᱜᱤᱫ ᱴᱚᱱ ᱥᱮᱴ ᱢᱮ ᱾ ᱟᱢ ᱡᱚᱛᱚᱱ ᱮᱢ ᱫᱚᱦᱚᱭᱟ ᱜᱚᱦᱚᱠ ᱠᱚ ᱪᱮᱫ ᱠᱚ ᱧᱮᱞᱟ ᱟᱨ ᱟᱢᱟᱜ ᱢᱟᱹᱱ ᱾ ᱟᱢᱟᱜ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱮᱴᱤᱝ ᱚᱰᱤᱴ ᱠᱟᱛᱮ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚᱦᱚ ᱠᱟᱜ ᱢᱮ᱾
ᱟᱢ ᱟᱢᱟᱜ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱟᱨ ᱥᱟᱱᱫᱮᱥ ᱨᱮᱭᱟᱜ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱵᱟᱵᱚᱛ ᱮᱢ ᱵᱷᱟᱵᱤᱭᱟ ᱾ ᱞᱟᱹᱠᱛᱤᱭᱟᱱ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱮᱴᱤᱝ ᱟᱨ ᱜᱷᱚᱴᱚᱠ ᱚᱰᱤᱴ ᱠᱟᱛᱮ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚᱦᱚᱭ ᱢᱮ᱾
Your product's reputation is impacted by your website. Keep your system secure by setting ideal settings and keeping the system updated.
ᱟᱢᱟᱜ ᱚᱱᱞᱟᱭᱤᱱ ᱢᱟᱹᱱ ᱫᱚ ᱟᱢᱟᱜ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱦᱚᱛᱮᱛᱮ ᱮᱥᱮᱨ ᱟᱠᱟᱱᱟ ᱾ ᱟᱢᱟᱜ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱟᱫᱷᱟᱨᱚᱱ ᱥᱮᱴᱤᱝ ᱥᱟᱶᱛᱮ ᱨᱟᱠᱷᱟ ᱫᱚᱦᱚᱭ ᱢᱮ ᱟᱨ ᱱᱚᱣᱟ ᱟᱯᱰᱮᱴ ᱫᱚᱦᱚᱭ ᱢᱮ ᱾
ᱟᱢ ᱴᱷᱮᱱ ᱟᱹᱰᱤ ᱠᱚᱢ ᱚᱠᱛᱚ ᱢᱮᱱᱟᱜᱼᱟ ᱢᱮᱱᱠᱷᱟᱱ ᱟᱢ ᱦᱚᱸ ᱡᱚᱛᱚᱱ ᱮᱢ ᱫᱚᱦᱚᱭᱟ ᱜᱚᱦᱚᱠ ᱠᱚ ᱪᱮᱫ ᱠᱚ ᱧᱮᱞᱟ ᱟᱨ ᱟᱢᱟᱜ ᱢᱟᱹᱱ ᱾ ᱟᱢᱟᱜ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱮᱴᱤᱝ ᱚᱰᱤᱴ ᱠᱟᱛᱮ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚᱦᱚ ᱠᱟᱜ ᱢᱮ᱾
ᱟᱢ ᱴᱷᱮᱱ ᱟᱹᱰᱤ ᱠᱚᱢ ᱚᱠᱛᱚ ᱢᱮᱱᱟᱜᱼᱟ ᱢᱮᱱᱠᱷᱟᱱ ᱟᱢ ᱦᱚᱸ ᱡᱚᱛᱚᱱ ᱮᱢ ᱫᱚᱦᱚᱭᱟ ᱜᱚᱦᱚᱠ ᱠᱚ ᱪᱮᱫ ᱠᱚ ᱧᱮᱞᱟ ᱟᱨ ᱟᱢᱟᱜ ᱢᱟᱹᱱ ᱾ ᱟᱢᱟᱜ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱮᱴᱤᱝ ᱚᱰᱤᱴ ᱠᱟᱛᱮ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚᱦᱚ ᱠᱟᱜ ᱢᱮ᱾
ᱟᱢᱟᱜ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱮᱴᱤᱝ ᱚᱰᱤᱴ ᱠᱟᱛᱮ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚᱦᱚ ᱠᱟᱜ ᱢᱮ᱾ ᱮᱴᱟᱜ ᱮᱴᱟᱜ ᱯᱮᱠᱮᱡᱽ ᱞᱮᱵᱮᱞ ᱠᱚ ᱟᱢ ᱞᱟᱹᱜᱤᱫ ᱵᱟᱹᱲᱛᱤ ᱡᱤᱱᱤᱥ ᱠᱚ ᱥᱟᱢᱵᱽᱲᱟᱣᱟ᱾
ᱟᱢᱟᱜ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱮᱴᱤᱝ ᱞᱚᱜᱚᱱ ᱚᱰᱤᱴ ᱠᱟᱛᱮ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚᱦᱚᱭ ᱢᱮ᱾ ᱟᱞᱮ ᱟᱢᱟᱜ ᱚᱠᱛᱚ ᱵᱟᱧᱪᱟᱣ ᱟᱨ ᱟᱢᱟᱜ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚᱦᱚ ᱞᱟᱹᱜᱤᱫ ᱠᱞᱟᱣᱰ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱟᱹᱱᱟᱹᱭᱠᱟᱹᱣ ᱟᱨ ᱫᱟᱲᱮ ᱥᱟᱶᱛᱮ ᱵᱮᱱᱟᱣ ᱟᱞᱜᱟ ᱵᱮᱵᱷᱟᱨ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱠᱚ ᱞᱮ ᱮᱢᱟᱢᱟ᱾
As a small business owner, you understand the importance of protecting your customers' data and your business's reputation. Keep your website secure by auditing your security settings with our easy-to-use tool.
ᱮᱴᱟᱜ ᱮᱴᱟᱜ ᱚᱵᱚᱥᱛᱟ ᱞᱟᱹᱜᱤᱫ ᱟᱭᱢᱟ ᱵᱮᱵᱷᱟᱨ
ᱮᱴᱟᱜ ᱠᱚ ᱥᱟᱶ ᱪᱮᱫ ᱞᱮᱠᱟ ᱵᱮᱵᱷᱟᱨ ᱦᱩᱭᱩᱜ-ᱟ ᱚᱱᱟ ᱫᱚ ᱑.᱖ ᱨᱮ ᱩᱫᱩᱜ ᱟᱠᱟᱱᱟ ᱾
| ᱥᱤ | ᱵᱤᱵᱨᱚᱬ |
|---|---|
ᱩᱫᱽᱭᱚᱜᱽ |
ᱟᱞᱮᱭᱟᱜ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱯᱷᱟᱭᱟᱨᱣᱟᱞ ᱟᱨ ᱚᱰᱤᱴ ᱴᱩᱞ ᱥᱟᱶ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱟᱞᱜᱟ ᱢᱮ |
ᱵᱞᱚᱜᱽᱜᱟᱨ |
ᱟᱢᱟᱜ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱴᱨᱟᱯᱷᱤᱠ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚᱦᱚᱭ ᱢᱮ |
ᱥᱤ ᱤ ᱳ ᱢᱩᱲᱩᱫ ᱠᱟᱹᱢᱤᱭᱟᱹ ᱟᱢᱞᱟ |
ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚ ᱟᱹᱰᱤ ᱞᱟᱹᱠᱛᱤᱭᱟᱱᱟᱜ ᱠᱟᱱᱟ |
ᱥᱤ ᱮᱢ ᱳ ᱢᱩᱲᱩᱫ ᱵᱟᱡᱟᱨ ᱟᱢᱞᱟ |
ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚ ᱢᱟᱹᱱ ᱨᱮ ᱮᱥᱮᱨ ᱮᱢᱟᱭᱟ |
ᱡᱤᱱᱤᱥ ᱢᱮᱱᱮᱡᱟᱨ |
ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱯᱨᱚᱰᱟᱠᱴ ᱨᱮ ᱮᱥᱮᱨ ᱮᱢᱟᱭᱟ |
ᱥᱚᱥᱤᱭᱟᱞ ᱢᱤᱰᱤᱭᱟ ᱯᱨᱚᱵᱷᱟᱵᱽ |
ᱨᱚᱯᱟ ᱨᱮ ᱛᱟᱦᱮᱱ ᱢᱮ ᱟᱨ ᱚᱱᱞᱟᱭᱤᱱ ᱨᱮ ᱛᱟᱦᱮᱱ ᱢᱮ |
ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱢᱟᱞᱤᱠ |
ᱟᱢᱟᱜ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚᱦᱚᱭ ᱢᱮ |
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱰᱮᱵᱷᱞᱚᱯᱟᱨ |
ᱟᱢ ᱛᱮᱭᱟᱨ ᱟᱠᱟᱫ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚᱦᱚᱭ ᱢᱮ |
ᱥᱤ ᱴᱤ ᱳ ᱢᱩᱲᱩᱫ ᱴᱮᱠᱱᱚᱞᱚᱡᱤ ᱟᱢᱞᱟ |
ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚ ᱚᱰᱤᱴ ᱦᱩᱭᱩᱜ ᱞᱟᱹᱠᱛᱤᱭᱟ |
ᱩᱫᱽᱭᱚᱜᱽ |
ᱨᱩᱠᱷᱤᱭᱟᱹ ᱩᱥᱟᱹᱨᱟ ᱞᱟᱹᱠᱛᱤᱜ ᱠᱟᱱᱟ |
ᱠᱟᱹᱴᱤᱡ ᱵᱮᱯᱟᱨ ᱢᱟᱞᱤᱠ |
ᱤᱧᱟᱜ ᱵᱮᱯᱟᱨ ᱞᱟᱹᱜᱤᱫ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚ ᱟᱹᱰᱤ ᱞᱟᱹᱠᱛᱤᱭᱟᱱᱟᱜ ᱠᱟᱱᱟ |
ᱠᱩᱠᱞᱤ ᱠᱚ ᱢᱮᱱᱟᱜᱼᱟ ?
ᱟᱞᱮ ᱟᱢᱟᱜ ᱠᱩᱠᱞᱤ ᱨᱮᱭᱟᱜ ᱛᱮᱞᱟ ᱮᱢ ᱠᱟᱛᱮ ᱠᱩᱥᱤ ᱢᱮᱱᱟᱜ ᱞᱮᱭᱟ᱾ ᱡᱩᱫᱤ ᱟᱢ ᱴᱷᱮᱱ ᱮᱴᱟᱜ ᱠᱩᱠᱞᱤ ᱠᱚ ᱛᱟᱦᱮᱱ ᱠᱷᱟᱱ ᱛᱟᱞᱠᱟ ᱧᱮᱞ ᱢᱮ ᱟᱨᱵᱟᱝᱠᱷᱟᱱ ᱤᱢᱮᱞ ᱞᱮᱢ᱾
ᱤᱧ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱮᱴᱤᱝ ᱪᱮᱫ ᱞᱮᱠᱟᱧ ᱵᱚᱫᱚᱞᱟ?
ᱟᱞᱮ ᱟᱞᱮᱭᱟᱜ ᱯᱮᱭᱰ ᱯᱞᱟᱜᱤᱱ ᱨᱮ ᱟᱯᱜᱽᱨᱮᱰ ᱞᱟᱹᱜᱤᱫ ᱞᱮ ᱢᱮᱛᱟᱢ ᱠᱟᱱᱟ ᱡᱟᱦᱟᱸ ᱛᱮ ᱟᱢ ᱟᱢᱟᱜ ᱥᱮᱴᱤᱝ ᱩᱥᱟᱹᱨᱟ ᱟᱨ ᱟᱞᱜᱟ ᱛᱮ ᱮᱰᱡᱟᱥᱴ ᱫᱟᱲᱮᱭᱟᱜᱼᱟᱢ᱾ ᱵᱟᱝᱠᱷᱟᱱ ᱟᱢ ᱟᱢᱟᱜ ᱠᱚᱱᱯᱷᱤᱜᱟᱨᱮᱥᱚᱱ ᱨᱮᱫ ᱠᱚ ᱨᱮ ᱢᱮᱱᱩᱣᱟᱞ ᱞᱮᱠᱟᱛᱮ ᱵᱚᱫᱚᱞ ᱫᱟᱲᱮᱭᱟᱜᱼᱟᱢ᱾
ᱪᱮᱫ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱚᱰᱤᱴ ᱯᱞᱟᱜᱤᱱ ᱢᱟᱭᱮᱥᱠᱩᱭᱮᱞ ᱥᱮ ᱢᱟᱨᱤᱭᱟᱰᱤᱵᱤ ᱥᱟᱶ ᱠᱟᱹᱢᱤᱭᱟ?
ᱦᱚᱭ ᱯᱞᱟᱜᱤᱱ ᱫᱚ ᱵᱟᱱᱟᱨ ᱰᱟᱴᱟᱵᱮᱥ ᱥᱤᱥᱴᱚᱢ ᱥᱟᱶ ᱠᱟᱹᱢᱤ ᱮᱫᱟᱭ ᱾
ᱪᱮᱫ ᱞᱮᱠᱟ ᱯᱷᱨᱟᱢ ᱚᱯᱥᱚᱱ ᱠᱚ ᱧᱮᱞ ᱠᱟᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮᱭᱟᱜ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱩᱫᱷᱨᱟᱹᱣ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ?
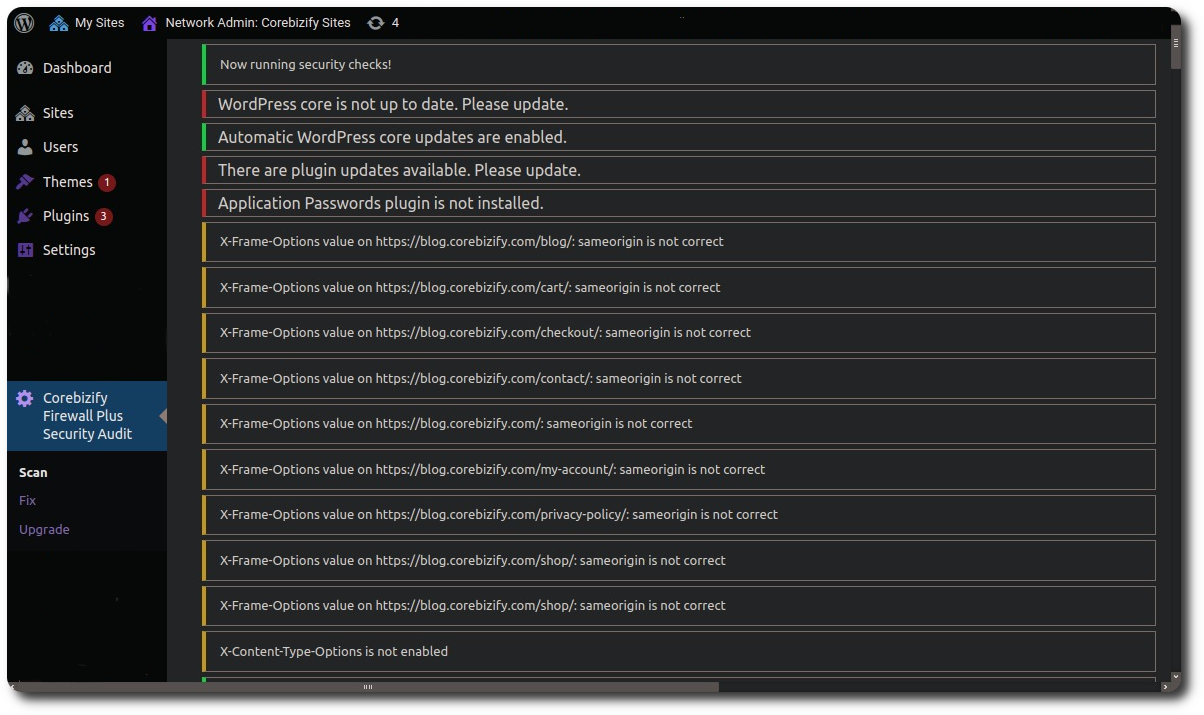
High risk. Clickjacking attacks can give attackers control over a user's clicks, potentially allowing them to steal sensitive information. Implementing X-Frame-Options header is crucial to prevent these attacks.
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱵᱟᱹᱜᱤ ᱯᱞᱟᱜᱽᱤᱱ ᱵᱟᱝ ᱧᱮᱞ ᱞᱮᱠᱷᱟᱱ ᱪᱮᱫ ᱵᱤᱯᱚᱫᱽ ᱢᱮᱱᱟᱜᱼᱟ?
ᱵᱟᱹᱲᱛᱤ ᱡᱷᱩᱠᱤ ᱾ ᱵᱟᱹᱜᱤ ᱟᱠᱟᱱ ᱥᱮ ᱢᱟᱨᱮ ᱯᱞᱟᱜᱤᱱ ᱠᱚ ᱫᱚ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱡᱷᱩᱠᱤ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ, ᱪᱮᱫᱟᱜ ᱥᱮ ᱱᱚᱶᱟ ᱯᱞᱟᱜᱤᱱ ᱠᱚ ᱨᱮ ᱵᱷᱩᱞ ᱠᱚ ᱫᱚ ᱟᱹᱰᱤ ᱜᱷᱟᱹᱲᱤᱡ ᱵᱟᱝ ᱯᱮᱪ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ ᱾
ᱡᱩᱫᱤ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱯᱤ ᱮᱪ ᱯᱤ ᱵᱷᱟᱨᱥᱚᱱ ᱵᱟᱝ ᱪᱮᱠ ᱞᱮᱱᱠᱷᱟᱱ ᱪᱮᱫ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ?
ᱵᱟᱹᱲᱛᱤ ᱡᱷᱩᱠᱤ ᱾ PHP ᱨᱮᱭᱟᱜ ᱢᱟᱨᱮ ᱵᱷᱟᱨᱥᱚᱱ ᱪᱟᱹᱞᱩ ᱠᱷᱟᱱ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱵᱷᱩᱞ ᱟᱨ ᱥᱚᱢᱵᱷᱚᱵᱚᱱ ᱟᱠᱨᱚᱢᱚᱱ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ᱾
ᱪᱮᱫ ᱞᱮᱠᱟ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱠᱚᱨ ᱵᱷᱟᱨᱥᱚᱱ ᱧᱮᱞ ᱠᱟᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱩᱫᱷᱨᱟᱹᱣ ᱞᱟᱹᱜᱤᱫ ᱜᱚᱲᱚ ᱧᱟᱢᱚᱜᱼᱟ?
ᱵᱟᱹᱲᱛᱤ ᱡᱷᱩᱠᱤ ᱾ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮᱭᱟᱜ ᱢᱟᱨᱮ ᱵᱷᱟᱨᱥᱚᱱ ᱪᱟᱹᱞᱩ ᱠᱟᱛᱮ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱫᱚ ᱵᱟᱰᱟᱭ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱮᱴᱠᱮᱴᱚᱬᱮ ᱠᱚ ᱞᱟᱹᱜᱤᱫ ᱵᱟᱝ ᱵᱟᱹᱲᱤᱡ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ ᱚᱠᱟ ᱫᱚ ᱱᱟᱶᱟ ᱵᱷᱟᱨᱥᱚᱱ ᱨᱮ ᱯᱮᱪ ᱟᱠᱟᱱᱟ᱾
ᱪᱮᱫ ᱞᱮᱠᱟ ᱛᱮ HSTS ᱧᱮᱞ ᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱞᱟᱵᱷ ᱧᱟᱢᱚᱜᱼᱟ?
ᱛᱟᱞᱟ ᱡᱷᱩᱠᱤ ᱾ HTTP Strict Transport Security (HSTS) ᱞᱟᱹᱜᱤᱫ ᱯᱨᱚᱴᱚᱠᱚᱞ ᱰᱟᱣᱱᱜᱽᱨᱮᱰ ᱟᱴᱠᱟᱨ ᱠᱷᱚᱱ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱞᱟᱹᱜᱤᱫ ᱫᱚ ᱟᱹᱰᱤ ᱡᱟᱹᱨᱩᱲ ᱜᱮᱭᱟ, ᱡᱟᱦᱟᱸ ᱫᱚ ᱟᱴᱠᱟᱨ ᱠᱚ ᱵᱮᱵᱚᱦᱟᱨ ᱟᱨ ᱵᱮᱵᱷᱟᱨ ᱠᱚ ᱞᱟᱹᱜᱤᱫ ᱫᱟᱣ ᱮᱢ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ᱾
ᱪᱮᱫ ᱞᱮᱠᱟ ᱛᱮ ᱠᱚᱨ ᱟᱯᱰᱮᱴ ᱧᱮᱞ ᱠᱟᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮᱭᱟᱜ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱩᱫᱷᱨᱟᱹᱣ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ?
ᱵᱟᱹᱲᱛᱤ ᱡᱷᱩᱠᱤ ᱾ ᱢᱟᱨᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱵᱷᱟᱨᱥᱚᱱ ᱠᱚ ᱫᱚ ᱟᱠᱨᱚᱢᱚᱱ ᱠᱚ ᱦᱚᱛᱮᱛᱮ ᱞᱚᱥᱚᱫᱚᱜ ᱠᱟᱱᱟ ᱚᱠᱚᱭ ᱫᱚ ᱵᱟᱰᱟᱭ ᱠᱟᱱ ᱵᱷᱩᱞᱱᱟᱨᱮᱵᱤᱞᱤ ᱠᱚ ᱞᱟᱜᱟᱣ ᱮᱫᱟ᱾ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱞᱟᱹᱜᱤᱫ ᱱᱟᱶᱟ ᱯᱷᱤᱪᱟᱨ ᱠᱚ ᱟᱨ ᱥᱩᱫᱷᱨᱟᱹᱣ ᱠᱚ ᱥᱟᱶᱛᱮ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱟᱯ ᱴᱩᱰᱮᱴ ᱫᱚᱦᱚ ᱫᱚ ᱟᱹᱰᱤ ᱞᱟᱹᱠᱛᱤᱭᱟᱱᱟᱜ ᱠᱟᱱᱟ ᱾
ᱡᱩᱫᱤ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱯᱞᱟᱜᱤᱱ ᱟᱯᱰᱮᱴ ᱵᱟᱝ ᱪᱮᱠ ᱞᱮᱱᱠᱷᱟᱱ ᱪᱮᱫ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ?
ᱵᱟᱹᱲᱛᱤ ᱡᱷᱩᱠᱤ ᱾ ᱢᱟᱨᱮ ᱯᱞᱟᱜᱤᱱ ᱵᱷᱟᱨᱥᱚᱱ ᱪᱟᱹᱞᱩ ᱫᱚ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱡᱷᱩᱠᱤ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ, ᱪᱮᱫᱟᱜ ᱥᱮ ᱱᱚᱶᱟ ᱯᱞᱟᱜᱤᱱ ᱨᱮ ᱵᱷᱩᱞᱱᱟᱨᱤᱴᱤ ᱠᱚ ᱫᱚ ᱟᱠᱨᱚᱢᱚᱱ ᱠᱚ ᱞᱟᱹᱜᱤᱫ ᱠᱚ ᱞᱟᱹᱜᱤᱫ ᱠᱟᱱᱟ᱾ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱞᱟᱹᱜᱤᱫ ᱱᱟᱶᱟ ᱯᱷᱤᱪᱟᱨ ᱠᱚ ᱟᱨ ᱥᱩᱫᱷᱨᱟᱹᱣ ᱠᱚ ᱥᱟᱶᱛᱮ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱟᱯ ᱴᱩᱰᱮᱴ ᱫᱚᱦᱚ ᱫᱚ ᱟᱹᱰᱤ ᱞᱟᱹᱠᱛᱤᱭᱟᱱᱟᱜ ᱠᱟᱱᱟ ᱾
ᱪᱮᱫ ᱞᱮᱠᱟ ᱛᱮ ᱒ ᱮᱯᱷ ᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮᱭᱟᱜ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱵᱟᱹᱲᱛᱤᱭᱟᱭ?
ᱛᱟᱞᱟ ᱡᱷᱩᱠᱤ ᱾ ᱵᱟᱨ ᱯᱷᱮᱠᱴᱚᱨ ᱚᱛᱷᱮᱱᱴᱤᱠᱮᱥᱚᱱ (2FA) ᱪᱟᱞᱟᱣ ᱫᱚ ᱵᱮᱵᱚᱦᱟᱨᱤᱭᱟᱹ ᱠᱚ ᱟᱠᱚᱣᱟᱜ ᱵᱮᱵᱚᱦᱟᱨᱤᱭᱟᱹ ᱧᱩᱛᱩᱢ ᱟᱨ ᱯᱟᱥᱣᱟᱨᱰ ᱥᱟᱶᱛᱮ ᱫᱚᱥᱟᱨ ᱯᱷᱚᱨᱢ ᱮᱢ ᱞᱟᱹᱜᱤᱫ ᱞᱟᱹᱠᱛᱤ ᱠᱟᱱᱟ᱾
ᱪᱮᱫ ᱞᱮᱠᱟ ᱛᱮ XML-RPC 2FA ᱪᱟᱹᱞᱩ ᱠᱟᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱞᱟᱵᱷ ᱧᱟᱢ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ?
Medium risk. Securing access to the website's resources through remote APIs is important, and enabling 2FA for XML-RPC authentication can provide an extra layer of security.
ᱮᱰᱢᱤᱱ ᱞᱚᱜᱤᱱ ᱭᱩᱟᱨᱮᱞ ᱧᱮᱞ ᱠᱟᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮᱭᱟᱜ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱪᱮᱫ ᱞᱮᱠᱟ ᱥᱩᱫᱷᱨᱟᱹᱣ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ?
ᱛᱟᱞᱟ ᱡᱷᱩᱠᱤ ᱾ ᱮᱰᱢᱤᱱᱤᱥᱴᱨᱮᱴᱚᱨ ᱞᱚᱜᱤᱱ ᱥᱟᱦᱴᱟ ᱞᱟᱹᱜᱤᱫ ᱠᱟᱥᱴᱚᱢ URL ᱵᱮᱵᱷᱟᱨ ᱠᱟᱛᱮ ᱰᱤᱯᱷᱚᱞᱴ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱞᱚᱜᱤᱱ ᱥᱟᱦᱴᱟ ᱞᱟᱹᱜᱤᱫ ᱟᱡ ᱛᱮ ᱟᱴᱠᱟᱨ ᱠᱚ ᱵᱚᱱᱫᱚ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ᱾
ᱪᱮᱫ ᱞᱮᱠᱟ ᱪᱤᱛᱟᱹᱨ ᱦᱚᱴᱞᱤᱝᱠᱤᱝ ᱧᱮᱞ ᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱞᱟᱵᱷ ᱧᱟᱢᱚᱜᱼᱟ?
Low risk. Preventing hotlinking can help reduce bandwidth usage and prevent others from using the website's images without permission.
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱵᱟᱹᱲᱛᱤ ᱯᱤᱮᱪᱯᱤ ᱨᱮᱫ ᱥᱟᱥᱟᱯᱲᱟᱣ ᱵᱟᱝ ᱧᱮᱞ ᱞᱮᱠᱷᱟᱱ ᱪᱮᱫ ᱵᱚᱛᱚᱨ ᱢᱮᱱᱟᱜᱼᱟ?
ᱵᱟᱹᱲᱛᱤ ᱡᱷᱩᱠᱤ ᱾ ᱵᱟᱹᱲᱛᱤ PHP ᱨᱮᱫ ᱥᱟᱥᱟᱯᱲᱟᱣ ᱚᱠᱟᱹᱡᱽᱣᱟᱹ ᱫᱚ ᱥᱮᱨᱵᱷᱟᱨ ᱨᱮ PHP ᱨᱮᱫ ᱠᱚ ᱥᱚᱫᱚᱨ ᱠᱷᱚᱱ ᱟᱠᱨᱚᱢᱚᱱ ᱠᱚ ᱵᱟᱝ ᱞᱟᱹᱜᱤᱫ ᱢᱤᱫ ᱵᱟᱹᱲᱛᱤ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱷᱟᱯ ᱠᱟᱱᱟ᱾ ᱡᱩᱫᱤ ᱱᱚᱣᱟ ᱯᱷᱤᱪᱟᱨ ᱵᱟᱝ ᱚᱠᱟᱹᱡᱽᱣᱟᱹ ᱞᱮᱱᱠᱷᱟᱱ, ᱱᱚᱣᱟ ᱫᱚ ᱟᱠᱨᱚᱢᱚᱱ ᱠᱚ ᱦᱚᱛᱮᱛᱮ ᱥᱮᱨᱵᱷᱟᱨ ᱨᱮ ᱵᱤᱱ ᱟᱹᱭᱫᱟᱹᱨᱤ ᱮᱠᱥᱮᱥ ᱦᱟᱢᱮᱴ ᱟᱨ ᱥᱮᱱᱥᱮᱴᱤᱵᱷ ᱵᱟᱯᱟᱰᱟᱭ ᱠᱩᱢᱲᱩ ᱞᱟᱹᱜᱤᱫ ᱠᱚ ᱵᱮᱵᱷᱟᱨ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ᱾
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱟᱭᱯᱷᱨᱮᱢ ᱵᱞᱚᱠᱤᱝ ᱵᱟᱝ ᱧᱮᱞ ᱞᱮᱠᱷᱟᱱ ᱪᱮᱫ ᱵᱤᱯᱚᱫᱽ ᱢᱮᱱᱟᱜᱼᱟ?
ᱛᱟᱞᱟ ᱡᱷᱩᱠᱤ ᱾ ᱵᱟᱦᱨᱮ ᱠᱷᱚᱱ iframes ᱵᱞᱚᱠ ᱠᱟᱛᱮ clickjacking ᱟᱴᱠᱟᱨ ᱠᱚ ᱵᱚᱱᱫᱚ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ ᱡᱟᱦᱟᱸ ᱫᱚ ᱟᱴᱠᱟᱨ ᱠᱚ ᱵᱮᱵᱚᱦᱟᱨᱤᱭᱟᱹ ᱠᱚᱣᱟᱜ ᱠᱞᱤᱠ ᱠᱚ ᱠᱚᱱᱴᱨᱚᱞ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ ᱟᱨ ᱥᱮᱱᱥᱤᱴᱤᱵᱷ ᱵᱮᱣᱨᱟ ᱠᱚ ᱠᱩᱢᱵᱽᱲᱩᱭ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ᱾ ᱢᱮᱱᱠᱷᱟᱱ, iframes ᱨᱮᱭᱟᱜ ᱠᱤᱪᱷᱩ ᱡᱟᱹᱨᱤ ᱵᱮᱵᱚᱦᱟᱨ ᱠᱚ ᱵᱚᱸᱫ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ, ᱟᱨ ᱱᱚᱶᱟ ᱫᱚ ᱯᱷᱩᱞᱯ ᱥᱚᱞᱦᱟ ᱵᱟᱝ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ ᱪᱮᱫᱟᱜ ᱥᱮ ᱟᱠᱨᱚᱢ ᱠᱚ ᱫᱚ ᱚᱱᱟ ᱯᱷᱚᱞᱚᱱ ᱧᱟᱢ ᱞᱟᱹᱜᱤᱫ ᱮᱴᱟᱜ ᱛᱟᱠᱱᱤᱠᱤ ᱠᱚ ᱵᱮᱵᱚᱦᱟᱨ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ᱾
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱚᱠᱟᱹᱡᱽᱣᱟᱹ ᱯᱷᱤᱰ ᱵᱟᱝ ᱧᱮᱞ ᱞᱮᱠᱷᱟᱱ ᱪᱮᱫ ᱚᱨᱡᱚ ᱦᱩᱭᱩᱜᱼᱟ?
ᱠᱚᱢ ᱡᱷᱩᱠᱤ ᱾ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱮ RSS ᱟᱨ Atom ᱯᱷᱤᱰ ᱠᱚ ᱚᱠᱟᱹᱡᱽᱣᱟᱹ ᱞᱮᱠᱷᱟᱱ ᱥᱮᱱᱥᱮᱴᱤᱵᱷ ᱵᱮᱣᱨᱟ ᱵᱟᱝ ᱵᱟᱰᱟᱭ ᱧᱟᱢ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ, ᱢᱮᱱᱠᱷᱟᱱ ᱱᱚᱶᱟ ᱫᱚ ᱵᱟᱝ ᱞᱟᱹᱠᱛᱤᱭᱟᱱ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱠᱟᱹᱢᱤ ᱠᱟᱱᱟ᱾ ᱯᱷᱤᱰ ᱪᱟᱹᱞᱩ ᱠᱟᱛᱮ ᱥᱩᱫᱷᱨᱟᱹᱣ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱴᱨᱟᱯᱷᱤᱠ ᱟᱨ ᱥᱮᱸᱫᱽᱨᱟ ᱤᱧᱡᱤᱱ ᱧᱮᱞᱚᱜ ᱞᱮᱠᱟᱱ ᱞᱟᱵᱷ ᱮᱢ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ᱾
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱩᱠᱩ ᱞᱚᱜᱤᱱ ᱥᱟᱦᱴᱟ ᱵᱟᱝ ᱧᱮᱞ ᱞᱮᱠᱷᱟᱱ ᱪᱮᱫ ᱵᱚᱛᱚᱨ ᱢᱮᱱᱟᱜᱼᱟ?
Medium risk. Using a hidden login page can make it more difficult for attackers to find the login page and launch automated attacks, but it may not be a foolproof solution. Attackers can still discover the login page through other means, such as through information disclosed in the website's source code.
ᱪᱮᱫ ᱞᱮᱠᱟ ᱛᱮ ᱯᱤᱝᱵᱮᱠ ᱦᱮᱰᱟᱨ ᱧᱮᱞ ᱠᱟᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱞᱟᱵᱷ ᱧᱟᱢᱚᱜᱼᱟ?
ᱠᱚᱢ ᱡᱷᱩᱠᱤ ᱾ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱮ ᱯᱤᱝᱵᱮᱠ ᱦᱮᱰᱟᱨ ᱠᱚ ᱪᱟᱹᱞᱩ ᱫᱚ DDoS ᱟᱴᱠᱟᱨ ᱞᱟᱹᱜᱤᱫ ᱵᱮᱵᱷᱟᱨ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ ᱟᱨ ᱡᱟᱦᱟᱸ ᱛᱤᱱ ᱦᱟᱹᱵᱤᱡ ᱵᱟᱝ ᱞᱟᱹᱠᱛᱤ ᱦᱩᱭᱩᱜ-ᱟ ᱾ ᱱᱚᱣᱟ ᱫᱚ ᱢᱤᱫ ᱢᱩᱲᱩᱫ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚ ᱵᱟᱝ ᱠᱟᱱᱟ, ᱢᱮᱱᱠᱷᱟᱱ ᱱᱚᱣᱟ ᱫᱚ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱫᱚ ᱱᱚᱣᱟ ᱯᱷᱤᱪᱟᱨ ᱵᱮᱵᱷᱟᱨ ᱨᱮᱭᱟᱜ ᱠᱚ ᱠᱩᱨᱩᱢᱩᱴᱩ ᱮᱫᱟ᱾
ᱪᱮᱫ ᱞᱮᱠᱟ ᱨᱮᱫ ᱥᱟᱥᱟᱯᱲᱟᱣ ᱧᱮᱞ ᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱞᱟᱵᱷ ᱧᱟᱢᱚᱜᱼᱟ?
ᱵᱟᱹᱲᱛᱤ ᱡᱷᱩᱠᱤ ᱾ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱰᱮᱥᱵᱚᱨᱰ ᱨᱮ ᱯᱷᱟᱭᱤᱞ ᱥᱟᱥᱟᱯᱲᱟᱣ ᱵᱟᱝ ᱛᱟᱦᱮᱱ ᱫᱚ ᱯᱞᱟᱜᱤᱱ ᱥᱮ ᱮᱴᱟᱜ ᱣᱮᱵᱽ ᱮᱯᱞᱤᱠᱮᱥᱚᱱ ᱨᱮ ᱯᱷᱟᱭᱤᱞ ᱥᱟᱥᱟᱯᱲᱟᱣ ᱠᱚ ᱵᱟᱝ ᱞᱟᱹᱜᱤᱫ ᱢᱤᱫ ᱥᱮᱬᱟ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱠᱟᱹᱢᱤ ᱠᱟᱱᱟ᱾ ᱨᱮᱫ ᱥᱟᱥᱟᱯᱲᱟᱣ ᱨᱮᱭᱟᱜ ᱟᱱᱫᱷᱟᱣ ᱮᱢ ᱠᱟᱛᱮ ᱥᱮᱨᱵᱷᱟᱨ ᱨᱮ ᱵᱟᱹᱲᱤᱡ ᱠᱚᱰ ᱟᱯᱞᱳᱰ ᱟᱨ ᱮᱠᱡᱤᱠᱭᱩᱴ ᱞᱟᱹᱜᱤᱫ ᱟᱠᱨᱚᱢᱚᱱ ᱠᱚ ᱮᱱᱮᱡ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ᱾
ᱪᱮᱫ ᱞᱮᱠᱟ wp-config ᱨᱮ ᱦᱩᱰᱟᱹᱜ ᱨᱤᱯᱚᱨᱴᱤᱝ ᱧᱮᱞ ᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱩᱫᱷᱨᱟᱹᱣ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ?
Medium risk. Verifying whether error reporting is disabled in the website's wp-config.php file is crucial for safeguarding sensitive information from being exposed through error messages. However, it may also pose a challenge in identifying and resolving errors on the website.
ᱪᱮᱫ ᱞᱮᱠᱟ ᱛᱮ ᱯᱤ ᱮᱪ ᱯᱤ ᱮᱠᱡᱤᱠᱭᱩᱥᱚᱱ ᱧᱮᱞ ᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮᱭᱟᱜ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱩᱫᱷᱨᱟᱹᱣ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ?
High risk. Confirming whether PHP code can be executed in the website's upload directories is essential for detecting and preventing attackers from uploading and running malicious code on the server.
ᱪᱮᱫ ᱞᱮᱠᱟ ᱛᱮ ᱛᱷᱤᱢ ᱵᱷᱟᱨᱥᱚᱱ ᱧᱮᱞ ᱠᱟᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱞᱟᱵᱷ ᱧᱟᱢᱚᱜᱼᱟ?
ᱛᱟᱞᱟ ᱡᱷᱩᱠᱤ ᱾ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱮ ᱤᱱᱥᱴᱚᱞ ᱟᱠᱟᱱ ᱛᱷᱤᱢ ᱠᱚ ᱫᱚ ᱢᱟᱨᱮ ᱵᱷᱟᱨᱥᱚᱱ ᱠᱚ ᱪᱟᱞᱟᱜ ᱠᱟᱱᱟ ᱥᱮ ᱵᱟᱝ ᱠᱟᱱᱟ ᱚᱱᱟ ᱧᱮᱞ ᱫᱚ ᱟᱹᱰᱤ ᱡᱟᱹᱨᱩᱲ ᱜᱮᱭᱟ, ᱪᱮᱫᱟᱜ ᱥᱮ ᱱᱚᱶᱟ ᱛᱷᱤᱢ ᱠᱚ ᱨᱮ ᱵᱟᱝ ᱯᱮᱪ ᱟᱠᱟᱱ ᱵᱷᱩᱞ ᱠᱚ ᱛᱟᱦᱮᱸ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ ᱡᱟᱦᱟᱸ ᱫᱚ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱠᱚ ᱟᱴᱠᱟᱨ ᱞᱟᱹᱜᱤᱫ ᱠᱚ ᱡᱷᱤᱡ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ᱾ ᱢᱮᱱᱠᱷᱟᱱ, ᱱᱚᱣᱟ ᱫᱚ ᱢᱟᱨᱟᱝ ᱡᱷᱩᱠᱤ ᱵᱟᱝ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ ᱡᱩᱫᱤ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱫᱚ ᱢᱟᱨᱮ ᱛᱷᱤᱢ ᱵᱟᱝ ᱵᱮᱵᱷᱟᱨ ᱮᱫ ᱠᱷᱟᱱ ᱾
ᱪᱮᱫ ᱞᱮᱠᱟ ᱯᱞᱟᱜᱤᱱ ᱤᱱᱴᱮᱜᱽᱨᱤᱴᱤ ᱧᱮᱞ ᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮᱭᱟᱜ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱩᱫᱷᱨᱟᱹᱣ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ?
ᱵᱟᱹᱲᱛᱤ ᱡᱷᱩᱠᱤ ᱾ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱮ ᱤᱱᱥᱴᱚᱞ ᱯᱞᱟᱜᱤᱱ ᱨᱮᱭᱟᱜ ᱯᱷᱟᱭᱤᱞ ᱪᱮᱠᱥᱟᱢ ᱯᱩᱥᱴᱟᱹᱣ ᱠᱟᱛᱮ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱮ ᱵᱟᱹᱲᱤᱡ ᱯᱞᱟᱜᱤᱱ ᱠᱚ ᱵᱟᱝ ᱵᱟᱹᱲᱤᱡ ᱞᱟᱹᱜᱤᱫ ᱢᱤᱫ ᱥᱮᱬᱟ ᱠᱟᱹᱢᱤ ᱠᱟᱱᱟ᱾
ᱤᱧ ᱪᱮᱫᱟᱜ ᱤᱧᱟᱜ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱚᱰᱤᱴ ᱞᱟᱹᱠᱛᱤᱭᱟᱹᱧ ᱠᱟᱱᱟ?
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱟᱭᱢᱟ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱮᱴᱤᱝ ᱢᱮᱱᱟᱜᱼᱟ ᱚᱠᱟ ᱫᱚ ᱰᱤᱯᱷᱚᱞᱴ ᱛᱮ ᱵᱟᱝ ᱪᱟᱹᱞᱩᱜᱼᱟ ᱾ ᱟᱢ ᱫᱚ ᱩᱱᱠᱩ ᱠᱷᱚᱱ ᱟᱭᱢᱟ ᱦᱚᱲ ᱵᱟᱢ ᱵᱟᱰᱟᱭ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ ᱾ ᱴᱩᱞ ᱫᱚ ᱟᱢᱟᱜ ᱥᱮᱴᱤᱝ ᱟᱨ ᱥᱚᱯᱷᱴᱣᱮᱭᱟᱨ ᱵᱷᱟᱨᱥᱚᱱ ᱨᱮᱭᱟᱜ ᱥᱴᱮᱴᱟᱥ ᱩᱫᱩᱜ ᱞᱟᱹᱜᱤᱫ ᱪᱮᱠ ᱪᱟᱹᱞᱩᱭᱟᱭ ᱾
ᱪᱮᱫ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱚᱰᱤᱴ ᱯᱞᱟᱜᱤᱱ ᱮᱱᱜᱤᱱᱮᱠᱥ ᱥᱮ ᱟᱯᱟᱪᱮ ᱥᱟᱶ ᱠᱟᱹᱢᱤ ᱮᱫᱟᱭ ᱥᱮ ?
ᱦᱚᱭ ᱯᱞᱟᱜᱤᱱ ᱫᱚ ᱮᱱᱜᱤᱱᱮᱠᱥ ᱟᱨ ᱟᱯᱟᱪᱮ ᱵᱟᱱᱟᱨ ᱥᱟᱶᱛᱮ ᱠᱟᱹᱢᱤᱭᱟ ᱾
ᱪᱮᱫ ᱯᱞᱟᱜᱤᱱ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱟᱲᱮ ᱥᱟᱶᱛᱮ ᱛᱮᱭᱟᱨ ᱞᱮᱱᱟ?
ᱦᱚᱭ ᱟᱞᱮ ᱴᱷᱮᱱ ᱮᱱᱴᱚᱨᱯᱨᱟᱭᱤᱡᱽ ᱞᱮᱵᱮᱞ ᱨᱮ ᱠᱞᱟᱣᱰ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱨᱮ ᱯᱟᱥᱱᱟᱣ ᱟᱹᱱᱟᱹᱭᱠᱟᱹᱣ ᱢᱮᱱᱟᱜᱼᱟ ᱾ ᱯᱞᱟᱜᱤᱱ ᱨᱮᱭᱟᱜ ᱢᱤᱫ ᱵᱷᱟᱹᱜᱤ ᱫᱚ ᱱᱚᱶᱟ ᱠᱟᱱᱟ ᱟᱢ ᱫᱚ ᱟᱢ ᱛᱮᱢ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱜᱟᱹᱠᱷᱩᱲᱤᱭᱟᱹ ᱦᱩᱭᱩᱜ ᱨᱮᱭᱟᱜ ᱞᱟᱹᱠᱛᱤ ᱵᱟᱹᱱᱩᱜᱼᱟ᱾
ᱪᱮᱫ ᱞᱮᱠᱟ ᱛᱮ ᱡᱤᱱᱤᱥ ᱞᱮᱠᱟᱱ ᱵᱤᱠᱚᱞᱯᱚ ᱧᱮᱞ ᱠᱟᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱞᱟᱵᱷ ᱧᱟᱢᱚᱜᱼᱟ?
ᱛᱟᱞᱟ ᱡᱷᱩᱠᱤ ᱾ ᱡᱟᱦᱟᱸ ᱞᱮᱠᱟ ᱩᱫᱩᱜ ᱟᱠᱟᱱᱟ ᱚᱱᱟ ᱠᱷᱚᱱ ᱵᱷᱮᱜᱟᱨ MIME ᱞᱮᱠᱟ ᱛᱮ ᱡᱤᱱᱤᱥ ᱵᱩᱡᱷᱟᱹᱣ ᱠᱟᱛᱮ ᱠᱨᱚᱥ ᱥᱟᱭᱤᱴ ᱥᱠᱨᱤᱯᱴᱤᱝ ᱞᱮᱠᱟᱱ ᱵᱷᱩᱞ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ᱾ ᱱᱚᱝᱠᱟᱱ ᱟᱠᱨᱚᱢᱚᱱ ᱵᱚᱱᱫᱚ ᱞᱟᱹᱜᱤᱫ ᱮᱠᱥ-ᱡᱤᱱᱤᱥ-ᱞᱮᱠᱟᱱ-ᱵᱤᱠᱚᱞᱯ ᱦᱮᱰᱟᱨ ᱞᱟᱹᱜᱩᱫ ᱫᱚ ᱟᱹᱰᱤ ᱞᱟᱹᱠᱛᱤᱭᱟᱱᱟᱜ ᱠᱟᱱᱟ ᱾
ᱪᱮᱫ ᱞᱮᱠᱟ ᱮᱠᱥᱮᱥᱮᱥ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱧᱮᱞ ᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱯᱞᱟᱜᱽᱤᱱ ᱟᱨᱦᱚᱸ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱵᱮᱱᱟᱣᱜᱼᱟ?
ᱛᱟᱞᱟ ᱡᱷᱩᱠᱤ ᱾ ᱠᱨᱚᱥ-ᱥᱟᱭᱤᱴ ᱥᱠᱨᱤᱯᱴᱤᱝ ᱟᱠᱨᱚᱢᱚᱱ ᱫᱚ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱮ ᱵᱟᱹᱲᱤᱡ ᱠᱚᱰ ᱤᱱᱡᱮᱠᱥᱚᱱ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ ᱟᱨ ᱵᱮᱵᱷᱟᱨᱤᱭᱟᱹ ᱰᱟᱴᱟ ᱠᱚ ᱥᱚᱢᱯᱚᱨᱢ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ᱾ ᱮᱠᱥ-ᱮᱠᱥᱮᱥᱮᱥ-ᱨᱚᱠᱷᱟ ᱦᱮᱰᱟᱨ ᱞᱟᱹᱜᱩ ᱠᱟᱛᱮ ᱱᱚᱝᱠᱟᱱ ᱟᱠᱨᱚᱢᱚᱱ ᱠᱷᱚᱱ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ᱾
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱢᱟᱭᱮᱥᱠᱭᱩᱮᱞ ᱵᱷᱟᱨᱥᱚᱱ ᱵᱟᱝ ᱧᱮᱞ ᱥᱟᱶ ᱪᱮᱫ ᱡᱷᱩᱠᱤ ᱡᱚᱲᱟᱣ ᱢᱮᱱᱟᱜᱼᱟ?
ᱵᱟᱹᱲᱛᱤ ᱡᱷᱩᱠᱤ ᱾ MySQL ᱨᱮᱭᱟᱜ ᱢᱟᱨᱮ ᱵᱷᱟᱨᱥᱚᱱ ᱵᱮᱵᱷᱟᱨ ᱠᱟᱛᱮ ᱦᱚᱸ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱵᱷᱩᱞ ᱟᱨ ᱥᱚᱢᱵᱷᱚᱵᱚᱱ ᱟᱠᱨᱚᱢᱚᱱ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ᱾
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱤᱱᱥᱴᱚᱞ ᱯᱞᱟᱜᱤᱱ ᱨᱮᱭᱟᱜ ᱵᱷᱟᱨᱥᱚᱱ ᱵᱟᱝ ᱧᱮᱞ ᱞᱮᱠᱷᱟᱱ ᱪᱮᱫ ᱚᱨᱡᱚ ᱦᱩᱭᱩᱜᱼᱟ?
ᱵᱟᱹᱲᱛᱤ ᱡᱷᱩᱠᱤ ᱾ ᱢᱟᱨᱮ ᱯᱞᱟᱜᱤᱱ ᱵᱷᱟᱨᱥᱚᱱ ᱪᱟᱹᱞᱩ ᱛᱮ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱵᱷᱩᱞ ᱟᱨ ᱥᱚᱢᱵᱷᱚᱵᱚᱱ ᱟᱠᱨᱚᱢᱚᱱ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ᱾
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱠᱩᱠᱤᱡᱽ ᱵᱟᱝ ᱧᱮᱞ ᱥᱟᱶ ᱪᱮᱫ ᱡᱷᱩᱠᱤ ᱡᱚᱲᱟᱣ ᱢᱮᱱᱟᱜᱼᱟ?
ᱛᱟᱞᱟ ᱡᱷᱩᱠᱤ ᱾ ᱠᱩᱠᱤ ᱠᱩᱢᱲᱩ ᱥᱮ ᱤᱱᱡᱮᱠᱥᱚᱱ ᱦᱚᱛᱮᱛᱮ ᱵᱮᱵᱷᱟᱨᱤᱭᱟᱹ ᱥᱮᱥᱚᱱ ᱰᱟᱴᱟ ᱠᱩᱢᱲᱩ ᱥᱮ ᱦᱮᱨᱟ ᱯᱷᱮᱨᱟ ᱠᱷᱚᱱ ᱟᱠᱨᱚᱢᱚᱱ ᱠᱚ ᱵᱚᱱᱫᱚ ᱞᱟᱹᱜᱤᱫ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱠᱩᱠᱤᱡᱽ ᱵᱮᱵᱷᱟᱨ ᱫᱚ ᱟᱹᱰᱤ ᱡᱟᱹᱨᱩᱲ ᱜᱮᱭᱟ᱾
ᱪᱮᱫ ᱞᱮᱠᱟ ᱟᱡ ᱛᱮ ᱪᱟᱞᱟᱜ ᱟᱯᱰᱮᱴᱟᱨ ᱧᱮᱞ ᱠᱟᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱞᱟᱵᱷ ᱧᱟᱢᱚᱜᱼᱟ?
High risk. Configuring the website's WordPress installation to automatically update to the latest version can ensure that security patches are applied in a timely manner, reducing the risk of vulnerabilities being exploited.
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱮᱯᱞᱤᱠᱮᱥᱚᱱ ᱯᱟᱥᱣᱟᱨᱰ ᱯᱞᱟᱜᱤᱱ ᱧᱮᱞ ᱫᱚ ᱪᱮᱫᱟᱜ ᱞᱟᱹᱠᱛᱤᱭᱟᱱᱟ?
Medium risk. Using the Application Passwords plugin is important for protecting user data and preventing unauthorized access to the website's resources.
ᱪᱮᱫ ᱞᱮᱠᱟ ᱞᱚᱜᱤᱱ ᱠᱮᱯᱴᱪᱟ ᱪᱮᱠᱤᱝ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮᱭᱟᱜ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱩᱫᱷᱨᱟᱹᱣ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ?
Medium risk. Using CAPTCHA on the website's login page can help prevent brute force attacks by requiring users to prove that they are human.
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱰᱤᱯᱷᱚᱞᱴ ᱮᱰᱢᱤᱱ ᱵᱮᱵᱷᱟᱨᱤᱭᱟᱹ ᱧᱩᱛᱩᱢ ᱵᱟᱝ ᱧᱮᱞ ᱞᱮᱠᱷᱟᱱ ᱪᱮᱫ ᱡᱷᱩᱠᱤ ᱢᱮᱱᱟᱜᱼᱟ?
ᱛᱟᱞᱟ ᱡᱷᱩᱠᱤ ᱾ ᱰᱤᱯᱷᱚᱞᱴ ᱣᱟᱨᱰᱯᱨᱮᱥ "ᱮᱰᱢᱤᱱ" ᱵᱮᱵᱷᱟᱨᱤᱭᱟᱹ ᱧᱩᱛᱩᱢ ᱵᱮᱵᱚᱦᱟᱨ ᱫᱚ ᱟᱠᱨᱚᱢ ᱠᱚ ᱞᱟᱹᱜᱤᱫ ᱢᱤᱫ ᱥᱟᱫᱷᱟᱨᱚᱱ ᱡᱚᱥ ᱠᱟᱱᱟ ᱪᱮᱫᱟᱜ ᱥᱮ ᱱᱚᱶᱟ ᱫᱚ ᱵᱟᱰᱟᱭ ᱰᱤᱯᱷᱚᱞᱴ ᱵᱮᱵᱷᱟᱨᱤᱭᱟᱹ ᱧᱩᱛᱩᱢ ᱠᱟᱱᱟ ᱚᱠᱟ ᱫᱚ ᱟᱹᱰᱤ ᱜᱷᱟᱹᱲᱤᱡ ᱵᱟᱝ ᱵᱚᱫᱚᱞᱚᱜ ᱠᱟᱱᱟ᱾ ᱱᱚᱣᱟ ᱵᱚᱫᱚᱞ ᱠᱟᱛᱮ ᱟᱨᱦᱚᱸ ᱵᱷᱮᱜᱟᱨ ᱫᱚ ᱢᱤᱫ ᱥᱮᱬᱟ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱷᱟᱯ ᱠᱟᱱᱟ ᱾
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱴᱮᱵᱩᱞ ᱯᱨᱤᱯᱷᱤᱠᱥ ᱵᱟᱝ ᱧᱮᱞ ᱥᱟᱶ ᱪᱮᱫ ᱡᱷᱩᱠᱤ ᱡᱚᱲᱟᱣ ᱢᱮᱱᱟᱜᱼᱟ?
ᱛᱟᱞᱟ ᱡᱷᱩᱠᱤ ᱾ ᱠᱟᱥᱴᱚᱢ ᱰᱟᱴᱟᱵᱮᱥ ᱴᱮᱵᱩᱞ ᱯᱨᱤᱯᱷᱤᱠ ᱵᱮᱵᱚᱦᱟᱨ ᱠᱟᱛᱮ ᱰᱟᱴᱟᱵᱮᱥ ᱴᱮᱵᱩᱞ ᱨᱮᱭᱟᱜ ᱧᱩᱛᱩᱢ ᱵᱟᱰᱟᱭ ᱞᱟᱹᱜᱤᱫ ᱟᱹᱰᱤ ᱢᱩᱥᱠᱤᱞ ᱠᱟᱛᱮ SQL ᱤᱱᱡᱮᱠᱥᱚᱱ ᱟᱴᱠᱟᱨ ᱠᱚ ᱵᱚᱱᱫᱚ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ᱾
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱯᱤᱮᱪᱯᱤ ᱨᱮᱫ ᱥᱟᱥᱟᱯᱲᱟᱣ ᱧᱮᱞ ᱪᱮᱫᱟᱜ ᱞᱟᱹᱠᱛᱤᱭᱟᱱᱟ?
High risk. Preventing attackers from modifying critical PHP files on the server through vulnerabilities in plugins or other web applications is crucial for the website's security. Allowing PHP file editing can enable attackers to upload and execute malicious code on the server.
ᱪᱮᱫ ᱞᱮᱠᱟ ᱛᱮ ᱠᱚᱢᱮᱱᱴ ᱠᱮᱯᱴᱪᱟ ᱧᱮᱞ ᱠᱟᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮᱭᱟᱜ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱵᱟᱹᱲᱛᱤᱜᱼᱟ?
Medium risk. Using a CAPTCHA on the website's comment form can help prevent automated spam comments, but it may not be a foolproof solution. Automated tools can bypass CAPTCHAs, and it can also inconvenience legitimate users who need to prove that they are human.
ᱪᱮᱫ ᱞᱮᱠᱟ ᱨᱟᱭᱤᱴ-ᱠᱞᱤᱠ ᱚᱠᱟᱹᱡᱽᱣᱟᱹ ᱧᱮᱞ ᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮᱭᱟᱜ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱩᱫᱷᱨᱟᱹᱣ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ?
ᱠᱚᱢ ᱡᱷᱩᱠᱤ ᱾ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱮ ᱨᱟᱭᱤᱴ-ᱠᱞᱤᱠ ᱚᱠᱟᱹᱡᱽᱣᱟᱹ ᱫᱚ ᱵᱮᱵᱷᱟᱨᱤᱭᱟᱹ ᱠᱚ ᱪᱤᱛᱟᱹᱨ ᱟᱨ ᱮᱴᱟᱜ ᱡᱤᱱᱤᱥ ᱠᱚ ᱠᱚᱯᱤ ᱥᱮ ᱥᱮᱵᱽ ᱠᱚ ᱵᱟᱝ ᱞᱟᱹᱜᱤᱫ ᱵᱮᱵᱚᱦᱟᱨ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ, ᱢᱮᱱᱠᱷᱟᱱ ᱱᱚᱶᱟ ᱫᱚ ᱯᱟᱹᱛᱤᱭᱟᱹᱣᱟᱱ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱠᱟᱹᱢᱤ ᱫᱚ ᱵᱟᱝ ᱠᱟᱱᱟ᱾ ᱜᱮᱭᱟᱱ ᱵᱮᱵᱷᱟᱨᱤᱭᱟᱹ ᱠᱚ ᱠᱤᱵᱚᱨᱰ ᱥᱚᱴᱠᱟᱴ ᱥᱮ ᱮᱴᱟᱜ ᱦᱚᱨᱟ ᱠᱚ ᱵᱮᱵᱷᱟᱨ ᱠᱟᱛᱮ ᱟᱞᱜᱟ ᱛᱮ ᱱᱚᱣᱟ ᱵᱟᱨᱚᱱ ᱠᱚ ᱵᱟᱭᱯᱟᱥ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ᱾
ᱯᱷᱮᱞ᱒ᱵᱮᱱ ᱪᱮᱫ ᱞᱮᱠᱟ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱞᱟᱵᱷ ᱧᱟᱢ ᱫᱟᱲᱮᱭᱟᱜᱼᱟᱭ?
High risk. Installing and configuring the Fail2Ban service on the website's server can help prevent brute force attacks by automatically blocking IP addresses that have repeatedly failed login attempts. Without this service, the website is at risk of being targeted by attackers attempting to guess user passwords.
ᱪᱮᱫ ᱞᱮᱠᱟ ᱛᱮ ᱪᱟᱹᱞᱩ ᱯᱤᱝᱵᱮᱠ ᱧᱮᱞ ᱛᱮ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱥᱩᱫᱷᱨᱟᱹᱣ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ?
ᱠᱚᱢ ᱡᱷᱩᱠᱤ ᱾ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱮ ᱯᱤᱝᱵᱮᱠ ᱪᱟᱞᱟᱣ ᱠᱟᱛᱮ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱴᱨᱟᱯᱷᱤᱠ ᱟᱨ ᱥᱮᱸᱫᱽᱨᱟ ᱤᱱᱡᱤᱱ ᱧᱮᱞ ᱞᱮᱠᱟ ᱞᱟᱵᱷ ᱧᱟᱢ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ, ᱢᱮᱱᱠᱷᱟᱱ ᱱᱚᱶᱟ ᱫᱚ DDoS ᱟᱴᱠᱟᱨ ᱞᱟᱹᱜᱤᱫ ᱦᱚᱸ ᱵᱮᱵᱚᱦᱟᱨ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ᱾ ᱱᱚᱣᱟ ᱫᱚ ᱢᱤᱫ ᱢᱩᱲᱩᱫ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱫᱚ ᱵᱟᱝ ᱠᱟᱱᱟ, ᱢᱮᱱᱠᱷᱟᱱ ᱱᱚᱣᱟ ᱫᱚ ᱚᱠᱟᱹᱡᱽᱣᱟᱹ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ ᱡᱩᱫᱤ ᱠᱷᱟᱥ ᱞᱟᱹᱠᱛᱤ ᱵᱟᱝ ᱦᱩᱭᱩᱜ ᱠᱷᱟᱱ ᱾
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱨᱮᱫ ᱥᱟᱥᱟᱯᱲᱟᱣᱤᱡ ᱵᱟᱝ ᱧᱮᱞ ᱞᱮᱠᱷᱟᱱ ᱪᱮᱫ ᱚᱨᱡᱚ ᱦᱩᱭᱩᱜᱼᱟ?
ᱵᱟᱹᱲᱛᱤ ᱡᱷᱩᱠᱤ ᱾ ᱣᱟᱨᱰᱯᱨᱮᱥ ᱰᱮᱥᱵᱚᱨᱰ ᱨᱮ ᱯᱷᱟᱭᱤᱞ ᱮᱰᱤᱴᱚᱨ ᱵᱟᱝ ᱛᱟᱦᱮᱱ ᱫᱚ ᱯᱞᱟᱜᱤᱱ ᱥᱮ ᱮᱴᱟᱜ ᱣᱮᱵᱽ ᱮᱯᱞᱤᱠᱮᱥᱚᱱ ᱨᱮ ᱵᱷᱩᱞ ᱠᱟᱛᱮ ᱥᱮᱨᱵᱷᱟᱨ ᱨᱮ ᱠᱨᱤᱴᱤᱠᱟᱞ PHP ᱯᱷᱟᱭᱤᱞ ᱠᱚ ᱵᱟᱝ ᱵᱟᱹᱲᱤᱡ ᱫᱟᱲᱮᱭᱟᱜ ᱠᱟᱱᱟ᱾ ᱨᱮᱫ ᱥᱟᱥᱟᱯᱲᱟᱣ ᱨᱮᱭᱟᱜ ᱟᱱᱫᱷᱟᱣ ᱮᱢ ᱠᱟᱛᱮ ᱥᱮᱨᱵᱷᱟᱨ ᱨᱮ ᱵᱟᱹᱲᱤᱡ ᱠᱚᱰ ᱟᱯᱞᱳᱰ ᱟᱨ ᱮᱠᱡᱤᱠᱭᱩᱴ ᱞᱟᱹᱜᱤᱫ ᱟᱠᱨᱚᱢᱚᱱ ᱠᱚ ᱮᱱᱮᱡ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ᱾
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱦᱩᱰᱟᱹᱜ ᱨᱤᱯᱳᱨᱴᱤᱝ ᱵᱟᱝ ᱧᱮᱞ ᱞᱮᱠᱷᱟᱱ ᱪᱮᱫ ᱪᱮᱫ ᱡᱷᱩᱠᱤ ᱢᱮᱱᱟᱜᱼᱟ?
ᱠᱚᱢ ᱡᱷᱩᱠᱤ ᱾ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱮ ᱦᱩᱰᱟᱹᱜ ᱨᱤᱯᱚᱨᱴᱤᱝ ᱚᱠᱟᱹᱡᱽᱣᱟᱹ ᱞᱮᱠᱷᱟᱱ ᱦᱩᱰᱟᱹᱜ ᱥᱟᱱᱫᱮᱥ ᱦᱚᱛᱮᱛᱮ ᱥᱮᱱᱥᱮᱴᱤᱵᱷ ᱵᱮᱣᱨᱟ ᱵᱟᱝ ᱥᱚᱫᱚᱨᱚᱜ ᱨᱮ ᱜᱚᱲᱚ ᱧᱟᱢᱚᱜᱼᱟ᱾ ᱢᱮᱱᱠᱷᱟᱱ, ᱱᱚᱣᱟ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱮ ᱮᱴᱠᱮᱴᱚᱬᱮ ᱥᱚᱞᱦᱮ ᱟᱨ ᱦᱩᱰᱟᱹᱜ ᱠᱚ ᱴᱷᱤᱠ ᱞᱟᱹᱜᱤᱫ ᱟᱨᱦᱚᱸ ᱟᱸᱴ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ᱾
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱴᱨᱟᱠᱵᱮᱠ ᱚᱠᱟᱹᱡᱽᱣᱟᱹ ᱨᱮᱭᱟᱜ ᱪᱮᱫ ᱞᱟᱵᱷ ᱢᱮᱱᱟᱜᱼᱟ?
ᱠᱚᱢ ᱡᱷᱩᱠᱤ ᱾ ᱱᱚᱶᱟ ᱯᱷᱤᱪᱟᱨ ᱥᱟᱶ ᱡᱚᱲᱟᱣ ᱥᱯᱟᱢ ᱟᱨ ᱮᱴᱟᱜ ᱵᱟᱹᱲᱤᱡ ᱠᱟᱹᱢᱤ ᱠᱚ ᱵᱟᱝ ᱛᱟᱦᱮᱱ ᱞᱟᱹᱜᱤᱫ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱮ ᱴᱨᱟᱠ ᱵᱮᱠ ᱵᱟᱝ ᱛᱟᱦᱮᱱ ᱠᱟᱱᱟ ᱚᱱᱟ ᱫᱚ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱮᱭᱟᱜ ᱡᱚᱛᱚ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱨᱮ ᱵᱟᱝ ᱵᱟᱹᱲᱤᱡ ᱮᱥᱮᱨ ᱵᱟᱝ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ᱾
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱴᱤᱢᱛᱷᱟᱢ ᱵᱟᱝ ᱧᱮᱞ ᱞᱮᱠᱷᱟᱱ ᱪᱮᱫ ᱵᱚᱛᱚᱨ ᱢᱮᱱᱟᱜᱼᱟ?
ᱛᱟᱞᱟ ᱡᱷᱩᱠᱤ ᱾ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱮ ᱴᱤᱢᱛᱷᱟᱢ ᱥᱠᱨᱤᱯᱴ ᱵᱮᱵᱚᱦᱟᱨᱚᱜ ᱠᱟᱱᱟ ᱥᱮ ᱵᱟᱝ ᱠᱟᱱᱟ ᱚᱱᱟ ᱧᱮᱞ ᱫᱚ ᱟᱹᱰᱤ ᱡᱟᱹᱨᱩᱲ ᱜᱮᱭᱟ, ᱪᱮᱫᱟᱜ ᱥᱮ ᱱᱚᱶᱟ ᱨᱮ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱠᱚ ᱵᱮᱵᱚᱦᱟᱨ ᱫᱟᱲᱮᱭᱟᱜ-ᱟ ᱾ ᱢᱮᱱᱠᱷᱟᱱ, ᱱᱚᱣᱟ ᱫᱚ ᱵᱟᱝ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ ᱡᱩᱫᱤ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱱᱚᱣᱟ ᱥᱠᱨᱤᱯᱴ ᱵᱟᱭ ᱵᱮᱵᱷᱟᱨ ᱮᱫ ᱠᱷᱟᱱ ᱾
ᱣᱟᱨᱰᱯᱨᱮᱥ ᱨᱮ ᱛᱷᱤᱢ ᱟᱯᱰᱮᱴ ᱵᱟᱝ ᱧᱮᱞ ᱞᱮᱠᱷᱟᱱ ᱪᱮᱫ ᱡᱷᱩᱠᱤ ᱢᱮᱱᱟᱜᱼᱟ?
ᱛᱟᱞᱟ ᱡᱷᱩᱠᱤ ᱾ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱮ ᱤᱱᱥᱴᱚᱞ ᱛᱷᱤᱢ ᱠᱚ ᱞᱟᱹᱜᱤᱫ ᱡᱟᱦᱟᱱ ᱟᱯᱰᱮᱴ ᱢᱮᱱᱟᱜ-ᱟ ᱥᱮ ᱵᱟᱝ ᱢᱮᱱᱟᱜ-ᱟ ᱚᱱᱟ ᱧᱮᱞ ᱫᱚ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱟᱨ ᱱᱟᱶᱟ ᱯᱷᱤᱪᱟᱨ ᱟᱨ ᱥᱩᱫᱷᱟᱹᱨ ᱠᱚ ᱞᱟᱹᱜᱤᱫ ᱟᱹᱰᱤ ᱞᱟᱹᱠᱛᱤᱭᱟᱱᱟ᱾ ᱢᱮᱱᱠᱷᱟᱱ, ᱱᱚᱣᱟ ᱫᱚ ᱢᱟᱨᱟᱝ ᱡᱷᱩᱠᱤ ᱵᱟᱝ ᱦᱩᱭ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ ᱡᱩᱫᱤ ᱣᱮᱵᱽᱥᱟᱭᱤᱴ ᱞᱟᱦᱟ ᱠᱷᱚᱱ ᱜᱮ ᱟᱯ-ᱴᱩᱰᱮᱴ ᱛᱟᱦᱮᱱ ᱠᱷᱟᱱ ᱾
ᱟᱨᱦᱚᱸ ᱠᱩᱠᱞᱤ ᱠᱚ ᱢᱮᱱᱟᱜᱼᱟ ? ᱟᱢᱟᱜ ᱠᱩᱠᱞᱤ ᱱᱚᱸᱰᱮ ᱠᱩᱞᱤᱭ ᱢᱮ
ᱤᱭᱩ ᱠᱩᱠᱤ ᱥᱚᱦᱢᱚᱛᱤ